Want to use an image from a private Docker registry as the base for GitLab Runner’s Docker executor?
GitLab CI/CD Examples This page contains links to a variety of examples that can help you understand how to implement GitLab CI/CD for your specific use case. Examples are available in several forms. As a collection of:.gitlab-ci.yml template files maintained in GitLab, for many common frameworks and programming languages. Use Docker to build Docker images. You can use GitLab CI/CD with Docker to create Docker images. For example, you can create a Docker image of your application, test it, and publish it to a container registry. To run Docker commands in your CI/CD jobs, you must configure GitLab Runner to support docker commands.
ECR example:
Full job:
Assuming the image exists on the registry, you can set the DOCKER_AUTH_CONFIG variable within your project’s Settings > CI/CD page:
The value of auth is a base64-encoded version of your username and password that you use to authenticate into the registry:
Continuing with the ECR example, you can generate a password using the following command:
To test, run:
Now, add the DOCKER_AUTH_CONFIG variable to your project’s Settings > CI/CD page:
Test out your build. You should see something similar to the following in your logs, indicating that the login was successful:
Gitlab Ci Python Docker Example
Unfortunately, we’re not done yet since the generated password/token from the get-login-password command is only valid for 12 hours. So, we need to dynamically update the DOCKER_AUTH_CONFIG variable with a new password. We can set up a new job for this:
Here, after exporting the appropriate environment variables (so we can access them in the aws_auth.sh script), we installed the appropriate dependencies, and then ran the aws_auth.sh script.
aws_auth.sh:
What’s happening?
- We generated a new password from the
get-login-passwordcommand and assigned it toAWS_PASSWORD - We then base64 encoded the username and password and assigned it to
ENCODED - We used jq to create the necessary JSON for the value of the
DOCKER_AUTH_CONFIGvariable - Finally, using a GitLab Personal access token we updated the
DOCKER_AUTH_CONFIGvariable
Make sure to add all variables you project’s Settings > CI/CD page.
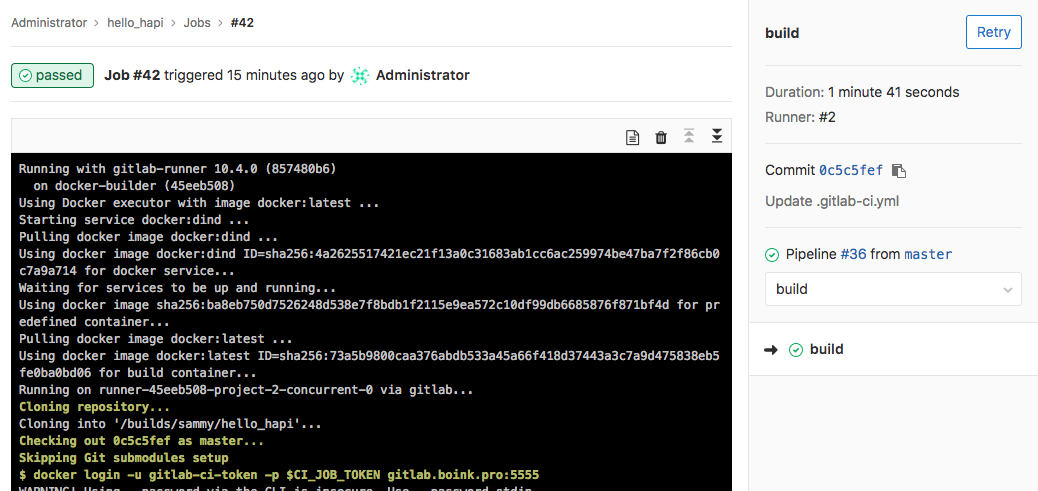
Now, the DOCKER_AUTH_CONFIG variable should be updated with a new password for each build.
That’s it!
–
Helpful Resources:
- GitLab Runner Issue Thread - Pull images from aws ecr or private registry
- GitLab Docs - Define an image from a private Container Registry
In the previous post I described how to run own GitLab server with CI runner.In this one, I’m going to walk through my experience of configuring GitLab-CI for one of my projects.I faced few problems during this process, which I will highlight in this post.
Some words about the project:
Gitlab Ci Python Docker Examples
- Python/Flask backend with PostgreSQL as a database, with the bunch of unittests.
- React/Reflux in frontend with Webpack for bundling. No JS tests.
- Frontend and backend are bundled in a single docker container and deployed to Kubernetes
Building the first container
First thing after importing repository into gitlab we need to create .gitlab-ci.yml.Gitlab itself has a lot of useful information about CI configuration,for example this andthis.
Previously I used to do following steps to test/compile/deploy manually:
- npm run build - to build all js/css
- build.sh - to build docker container
- docker-compose -f docker-compose-test.yml run –rm api-test nosetests
- deploy.sh - to deploy it
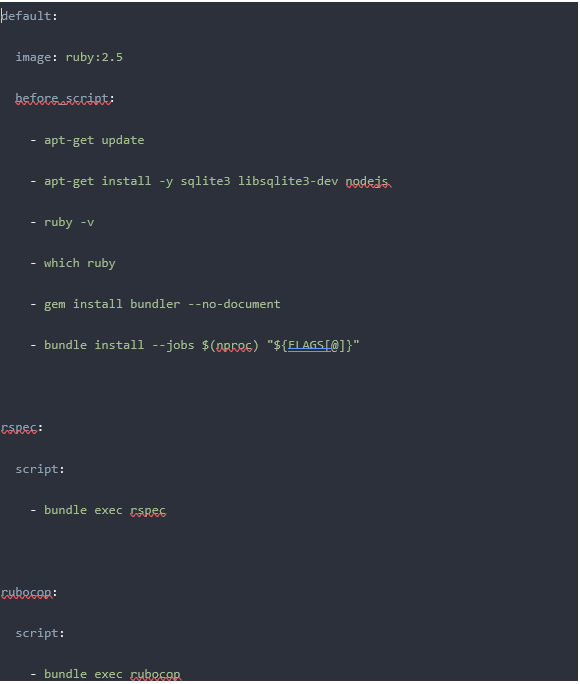
Everything is pretty common for most of the web projects.So, I started with a simple .gitlab-ci.yml file, trying to build my python code:
$CI_BUILD_TOKEN- is a password for my docker registry, saved in projects variables in GitLab project settings
And it actually worked fine. I got my docker container built and pushed to the registry.Next step was to be able to run tests. This is where things became not so obvious.For testing, we need to add another stage to our gitlab-ci file.

Testing. First try
After reading posts like thisI thought that it will be as easy as declaring service and adding test stage:
But it didn’t work. As far as I understood it, it’s because of docker-in-docker runner.Basically, we have 2 containers - docker:latest and postgresql:9.5, and they are linked perfectly fine.But then we’re bootstrapping our own container, inside this docker container.And this container can’t use docker links to access postgres, because its outside of its scope.
Testing. Second try
Then I tried to use my container as and image for the test stage and service declared in test stage itself, like this:
But it also didn’t work because of authentication.
My docker registry needs authentication which I do in before_script stage. But before_script is being called after the services.I assume that this method should work for public images.
Testing. Third try. Kinda working solution
So I decided to try to use docker-compose in tests as I was doing manually since.Docker-compose should be able to run and link everything together.And since this page in documentation says:
GitLab CI allows you to use Docker Engine to build and test docker-based projects.
This also allows to you to use docker-compose and other docker-enabled tools.
I was very confused when I was not able to use docker-compose, since docker:latest image has no docker-compose installed.I spent some time googling and trying to install compose inside the container,and ended up using image jonaskello/docker-and-compose instead of the recommended one.
So my test stage changed to this:
Gitlab Ci Cd Python Docker
This actually worked, but from time to time I was seeing weird race conditions during database provisioning.It’s not a big problem, and could be fixed easily. But I decided to try one more approach.
Testing. Final version
This time I decided to run postgres container during the test stage and link it to my test container.This requires to provide additional configuration to postgres container, but still this way is the closest to the original services approach.
Now, when we have our python container built and tested we need to add one more thing.We need to compile our javascript and css and put it into release container.This stage is actually going before the build.To be able to use files between stages we need to use some cache.In my case we need to cache only one directory.The one where webpack produces compiled files - src/static/dist.
Cache is described in more details in official docs
As for release stage I’m simply going to tag container with build number and push it back to the registry.
Now we have a working CI pipeline which can build a container, run tests against this container and then push it to the registry.So far so good. The only problem is that all of this takes very long time. For my project, it takes about 20 minutes to finish all these stages.Most of the time is spent on building docker layers, downloading python and npm packages and installing it.Next post will probably be about reducing this time by using some local caching services.